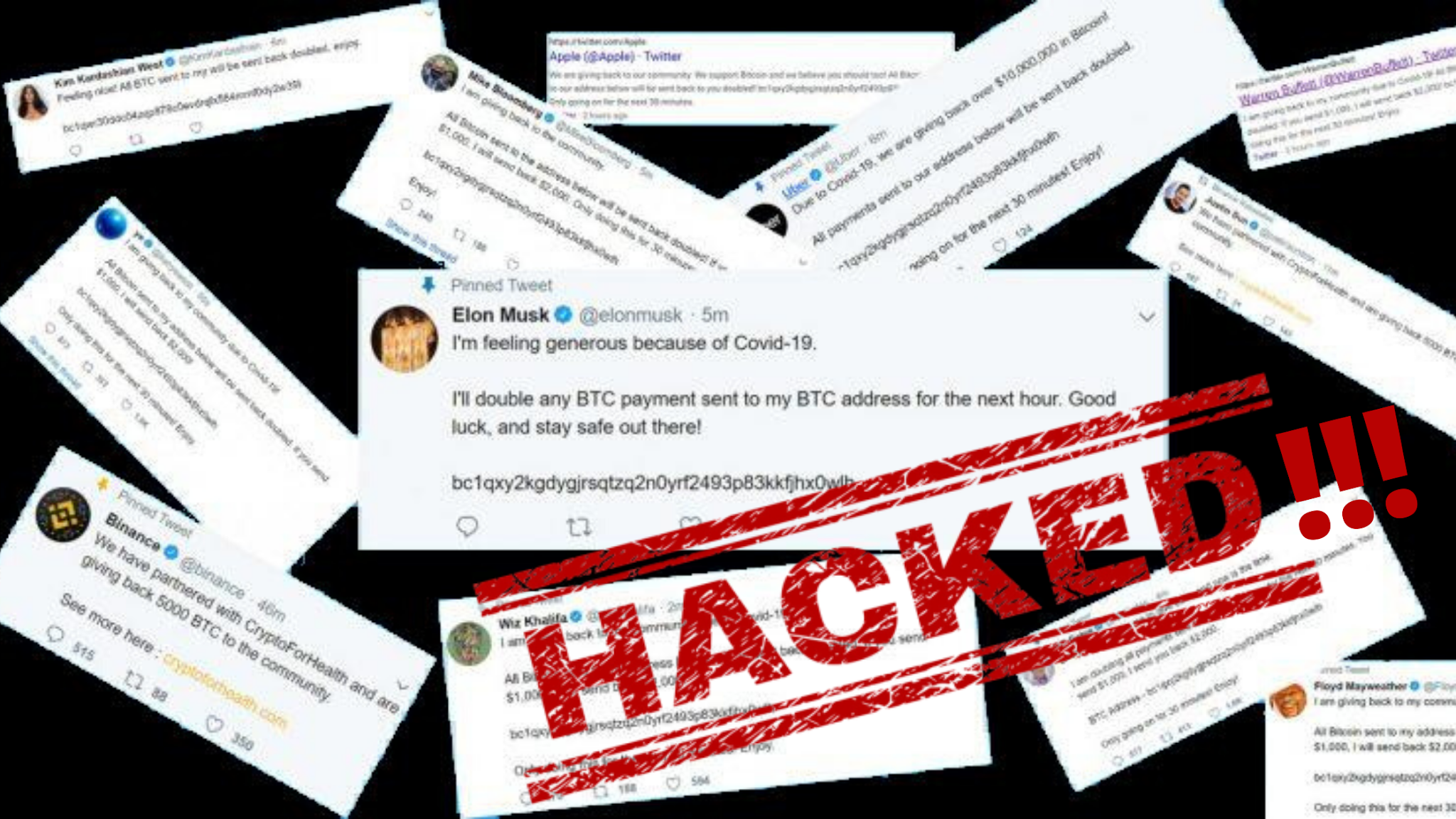
The digital world is a fascinating yet perilous landscape, where a single vulnerability can lead to catastrophic consequences. The term "twitter hacked" has become a chilling phrase in recent years, as high-profile accounts have fallen prey to malicious actors. This alarming trend reveals the dark side of social media, where information can be manipulated, reputations tarnished, and trust eroded in an instant. As users of this platform, we must remain vigilant and informed about the potential dangers that lurk behind our screens.
In this article, we will explore the various facets of the "twitter hacked" phenomenon, examining not only the incidents themselves but also the implications for both individuals and society as a whole. From the motivations behind these hacks to the methods employed by cybercriminals, we will delve into the intricate web of deceit that characterizes this digital age. Furthermore, we will discuss the steps that can be taken to safeguard ourselves and our accounts, ensuring that we remain one step ahead of those who seek to exploit our online presence.
As we navigate the complexities of this digital landscape, understanding the dynamics of "twitter hacked" incidents is crucial for anyone who engages with social media. Whether you're a casual user or a prominent figure, the risks are ever-present, and knowledge is your best defense. So, let's embark on this journey together, uncovering the truth and arming ourselves with the information necessary to protect our digital identities.
What Happened During the Major Twitter Hacking Incident?
The "twitter hacked" incident that made headlines involved a coordinated attack on several high-profile accounts, including those of celebrities, politicians, and businesses. The hackers exploited vulnerabilities in Twitter's systems to gain unauthorized access and post misleading content, often soliciting cryptocurrency donations. This incident raised serious concerns about the security protocols in place and the potential ramifications of such breaches.
Who Were the Victims of the Twitter Hack?
Notable victims of the "twitter hacked" incident included:
- Barack Obama
- Elon Musk
- Joe Biden
- Bill Gates
- Kanye West
This high-profile list of victims highlighted the severity of the attack and its potential impact on public trust in social media platforms.
What Motivated the Hackers?
The motivations behind the "twitter hacked" incident appeared to be both financial and attention-seeking. By exploiting the trust associated with these prominent accounts, the hackers aimed to trick users into sending money in cryptocurrency. Additionally, the notoriety gained from such a high-profile hack could serve to bolster the hackers' reputation within the underground cyber community.
How Did the Hackers Gain Access to Twitter Accounts?
The hackers utilized a sophisticated approach to gain access to the targeted accounts. Reports indicated that they employed social engineering techniques, manipulating Twitter employees to provide them with sensitive information. Additionally, they exploited vulnerabilities within Twitter's internal systems, allowing them to bypass standard security measures.
What Were the Consequences of the Twitter Hack?
The consequences of the "twitter hacked" incident were far-reaching. Beyond the immediate financial losses incurred by users who fell victim to the scam, the incident raised questions about the effectiveness of Twitter's security measures. It also sparked discussions about the need for better regulations surrounding social media platforms and the responsibility they hold to protect their users.
How Can Users Protect Themselves from Future Hacks?
In light of the "twitter hacked" incident, users must take proactive steps to safeguard their accounts:
- Enable two-factor authentication to add an extra layer of security.
- Regularly update passwords and use strong, unique combinations.
- Be cautious of unsolicited messages or requests for personal information.
- Monitor account activity for any unauthorized changes.
What Is Twitter Doing to Improve Security?
In response to the "twitter hacked" incident, Twitter has taken measures to enhance its security protocols. These improvements include:
- Implementing more stringent verification processes for employees.
- Increasing transparency regarding security incidents and their outcomes.
- Providing users with better resources to understand potential threats.
These steps are essential for restoring user confidence and ensuring the platform remains a safe space for communication.
Can We Trust Twitter Again?
The question of trust in the aftermath of the "twitter hacked" incident is a complex one. While Twitter has made strides to improve security, the lingering doubt remains. Users must weigh the benefits of social media engagement against the potential risks and make informed decisions about their online presence.
What Can We Learn from the Twitter Hacked Incident?
The "twitter hacked" incident serves as a stark reminder of the vulnerabilities inherent in our increasingly digital lives. It underscores the importance of vigilance, education, and proactive measures when engaging with social media platforms. By understanding the risks and taking appropriate precautions, users can better protect themselves and contribute to a safer online environment.
Biography of a Key Victim: Barack Obama
Barack Obama, the 44th President of the United States, was among the notable victims of the "twitter hacked" incident. His account was compromised, leading to a series of fraudulent tweets that misled followers.
| Name | Barack Obama |
|---|---|
| Date of Birth | August 4, 1961 |
| Nationality | American |
| Political Party | Democratic |
| Years in Office | 2009 - 2017 |
As a public figure with a massive following, Barack Obama's account was particularly appealing to hackers seeking to exploit his influence. This incident not only impacted him personally but also raised awareness about the vulnerabilities faced by public figures in the digital age.
In conclusion, the "twitter hacked" incident serves as a critical case study in the realm of cybersecurity. It illustrates the need for continuous improvement in security measures, user awareness, and the overall integrity of social media platforms. By learning from these incidents, we can work towards creating a safer online environment for all users.